Unlike industry common practice, where consultants rush blindly into a client, throw bodies that lack the necessary knowledge at the problem, move problems around and provide subpar ‘solutions’ unworthy of the word, we partner with our clients employing Design Thinking, a methodology that provides a customer-centric solution-based approach to problem-solving. With this iterative methodology, we are able to fully engage with our clients to Empathize on the challenges as though we are the client, we capture the essence of the challenges and Define it along with the client, then Collaborate or ideate as necessary on possible solutions or Prototypes that we Test and/or combine as necessary to Deliver the ultimate solution that fits the use case.
Our personnel are not only professionals in the core subject matter but also in our approach to problem-solving to provide insights beyond our clients’ imagination so that whoever is engaged with clients is delivering on our promise. This is our value proposition.
Security & Privacy
With seasoned information security & privacy professionals, we can help ensure your infrastructure meets security & privacy requirements unique to your environment(s). Learn more
Compliance
We have the expertise and experience to ensure compliance with the myriad of frameworks as well as corresponding risk and vulnerability management. Learn more
Cloud Security & Strategy
With seasoned multi-cloud professionals armed with best practices cloud adoption framework, we ensure the strategy & roadmap to your secure cloud is as seamless as you’d like it to be. Learn more
Assessments
We assess hosts, databases, and web applications to identify potential configuration and other deficiencies so appropriate mitigations are formulated & implemented. Learn more
Secure Apps/Systems Development
Whether its an application or enterprise infrastructure, we can help securely plan, build/deploy, and manage them in compliance with pertinent security requirements. Learn more
Managed Services
We effectively manage, detect, and respond to network threats on your on-premises and cloud infrastructure(s) before they affect your business so you can rest assured. Learn more
Advisory Services
We provide risk management; governance, compliance, assurance; security & privacy; third-party risk; threat and vulnerability management; cyber breach services., etc. Learn more
Threat Modeling
Identify security requirements unique to your infrastructure through threat modeling and attack simulation to implement appropriate controls and as part of monitoring strategy. Learn more
Penetration Testing
Black-, gray-, or white-box internal and/or external pen-testing from attackers’ viewpoint(s) to discover, identify, remediate, and continuously monitor critical vulnerabilities. Learn more
Incident Response
Ensuring due diligence and due care before, during, and after an incident throughout the identify > protect > detect > respond > recover process is our specialty. Learn more
Virtual CISO (vCISO)
With seasoned information security knowledge and security expertise, our on-site or remote virtual CISOs assume the role as part of your team, on a fulltime basis or otherwise. Learn more
Security & Compliance Automation
We accelerate your time to market with pre-built and secure cloud environment in a day, at minimal cost, compliant, and audit-ready for frameworks such as FedRAMP, CMMC, HIPAA, ISO, etc. Learn more
CMMC
Prepare and certify that your infrastructure meets one of the (DoD) CMMC levels of compliance requirements for security required to secure your and tyour customers’ information. Learn more
SecDevOps
Our expertise is Integrating secure development best practices and methodologies into development & operations processes in everything we do. Let us put security first for your organization. Learn more
FedRAMP
Get FedRAMP-authorized in record time, ensure ongoing compliance and security, ongoing and annual assessments, continuous monitoring, and vulnerability management. Learn more
WHAT’S OUR APPROACH?
Layered security + continuous monitoring + continuous improvement.
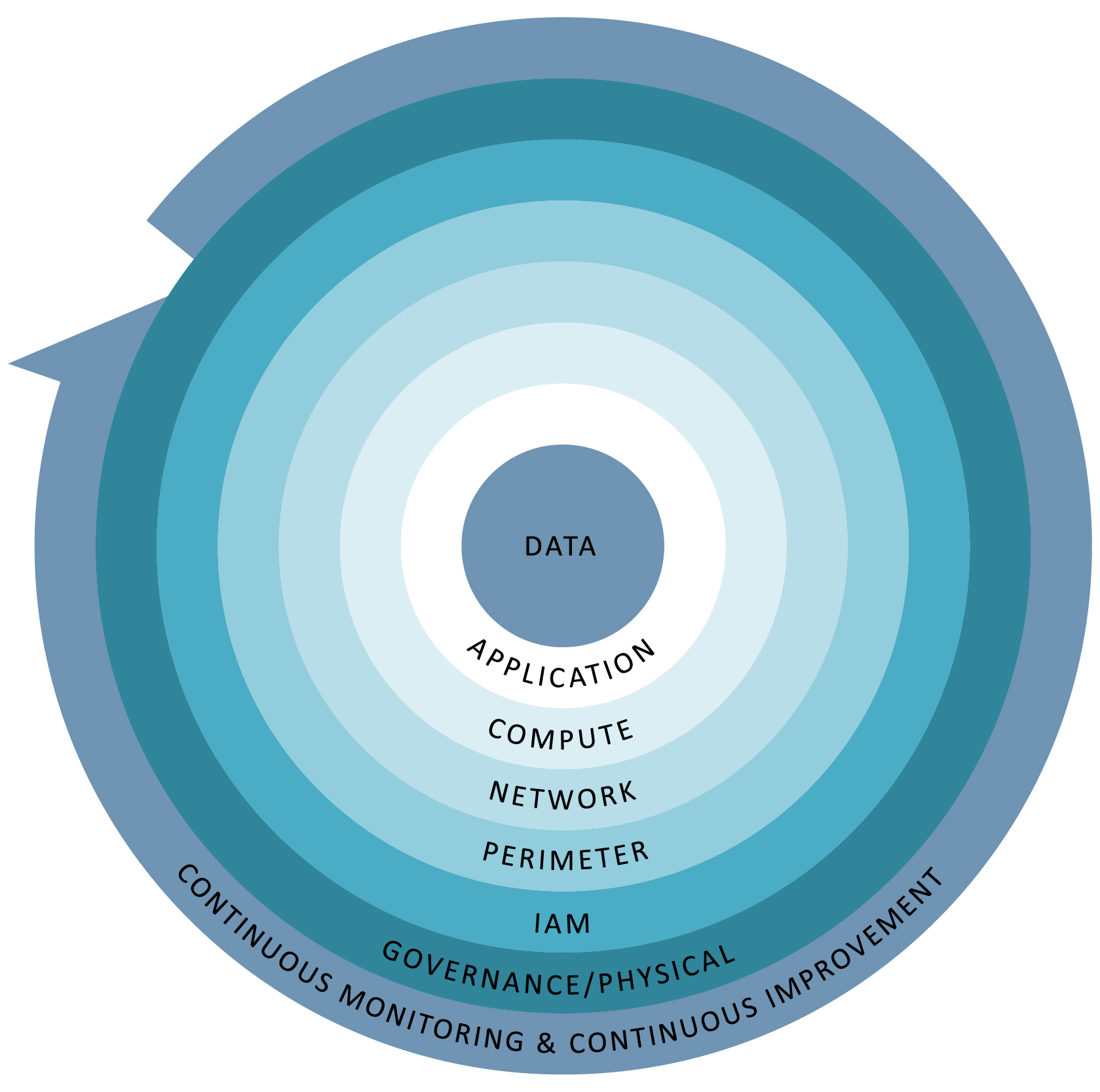
Our layered security approach across your Corporate, Development, and Operations environments for a seamless end-to-end security framework.
Governance/physical security layer your organization’s information assets, governance, risk management, and compliance program needs.
IAM layer is where zero trust identity infrastructure is designed to ensure decision/enforcement points.
Perimeter layer continuously monitor your assets to timely detect anomalies & events and understand the potential impact.
Network layer swiftly respond accordingly to contain any impact of potential cybersecurity incidents.
Application layer support efforts to quickly recover assets to normal operations to reduce the impact from a cybersecurity incident.
Data layer apply agile continuous improvement methodologies to ensure the ever-evolving threat landscape is mitigated.
Continuous monitoring and Continuous improvement Data apply agile continuous improvement methodologies to ensure the ever-evolving threat landscape is mitigated.
Frequently asked questions
What is baseline?
Baseline is the minimum security requirement to meet the needs of a certain security framework such as FedRAMP, NIST, PCI-DSS, etc.
What is security?
Security is the higher threshold beyond baseline requirements with additional security controls to address unique requirements of the intended infrastructure.
Baseline vs Security
Methodologies such as threat modeling are used to determine additional controls to address unique requirements to meet a higher threshold beyond baseline requirements.
How do we become compliant?
An initial assessment would be required to determine the gap between the current and desired states of your baseline and security requirements to determine necessary steps.
How do we become more secure?
Threat modelling is an effective methodology that identifies unique security controls to ultimately secure your data flow as a part of your security and continuous monitoring strategy.
What can happen if we’re neither?
If you neither meet baseline requirements for any framework nor security requirements for your unique infrastructure, you are most vulnerable to compromise and resultant consequences.
How can I avoid all of this?
Due diligence of assessing the current state of your security and due care to address it to the extent possible are the ultimate responsibilities of each organization’s executives.
Can secureloop make us secure?
We are specialists in the compliance with security framework baslines as well as helping organizations attain that higher threshold of security for their unique infrastructure.
How is secureloop better than others?
We employ customer-centered design thinking approach to understand and reframe your challenges and ideate on solution(s) to implement to achieve the intended outcomes.
Get a complete compliance and/or security audit!
See how far you are from reaching your risk management objective(s).






