
Why should organizations’ information systems be CMMC-compliant?
Contractors and sub-contractors of the DoD and soon, other agencies with sensitive information, no matter the org’s position in the food chain, MUST secure their environments to CMMC standards that maximizes business exposure. Learn more.
THE PERILOUS STATE OF INFORMATION SECURITY
Data breach incidents across small, medium, and large organizations are rising exponentially.
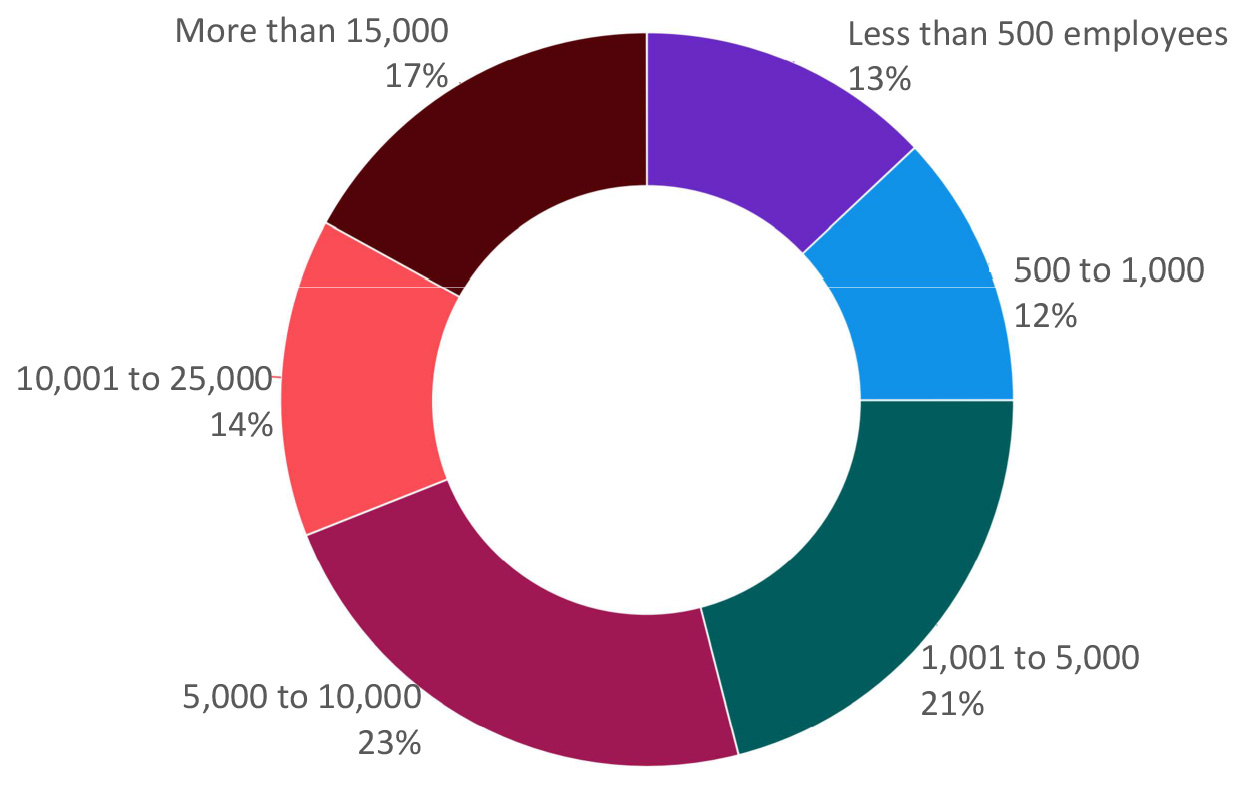
Distribution of all 524 organizations impacted by malicious attacks by size.
With the increase from 42% to 52% in malicious attacks on organizations between 2014 and 2020, businesses of all sizes and across industries are represented in double digits and are expected to continue the upward trend, according to IBM Cost of Data Breach Report.
Some of these malicious attacks have compromised and leveraged contractor systems in attacking government agency systems, hence the introduction of CMMC (by the DoD and imminent adoption by other agencies) to address contractor information systems security.
This is, however, recommended for every organization to better safeguard their environments, brand, revenue, etc.
MITIGATE THE RISK OF DATA BREACHES IN YOUR ORGANIZATION
Drastically reduce risks in your operating environments.
Evaluate business needs and objective as well as relevant contract engagements and desired exposure to determine which CMMC level is appropriate to attain.
Conduct a readiness assessment and gap analysis to gain detailed understanding of gaps to meeting the requirements of the target CMMC level.
Develop a remediation plan (aka a POAM or Risk Register), a prioritized, actionable plan of record to address security gaps uncovered during the Readiness Assessment and bring the organization into CMMC compliance.
Develop a System Security Plan (SSP) and relevant attachments, living artifacts that represent the ongoing security state of an organization’s systems & operating environments, which must be continuously updated with any change made to their security profile.
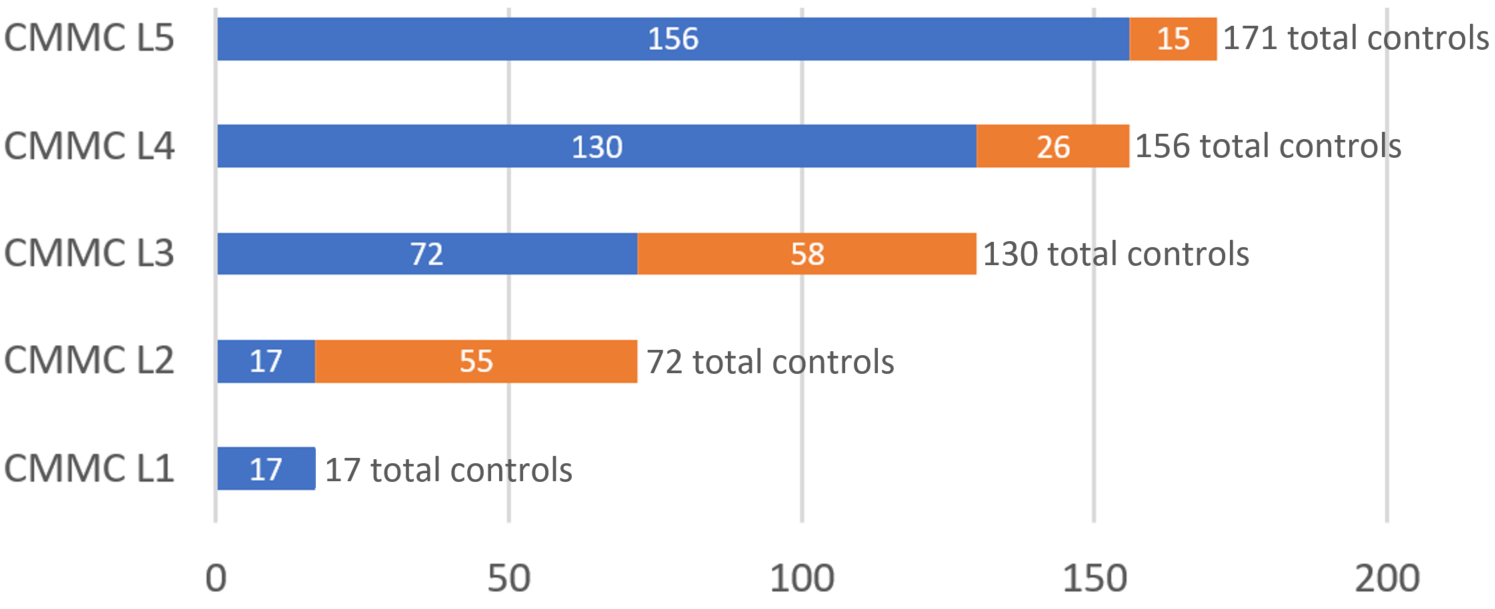
The five levels of CMMC (L1 being the lowest)
Use tools to continuously protect and monitor the security profile of pertinent systems.
Use managed security services to help close the security skills gap or handle the entire process to offload and avoid burdening your in-house personnel.
WHY HIRE US?
We are best in class in information security/managed services
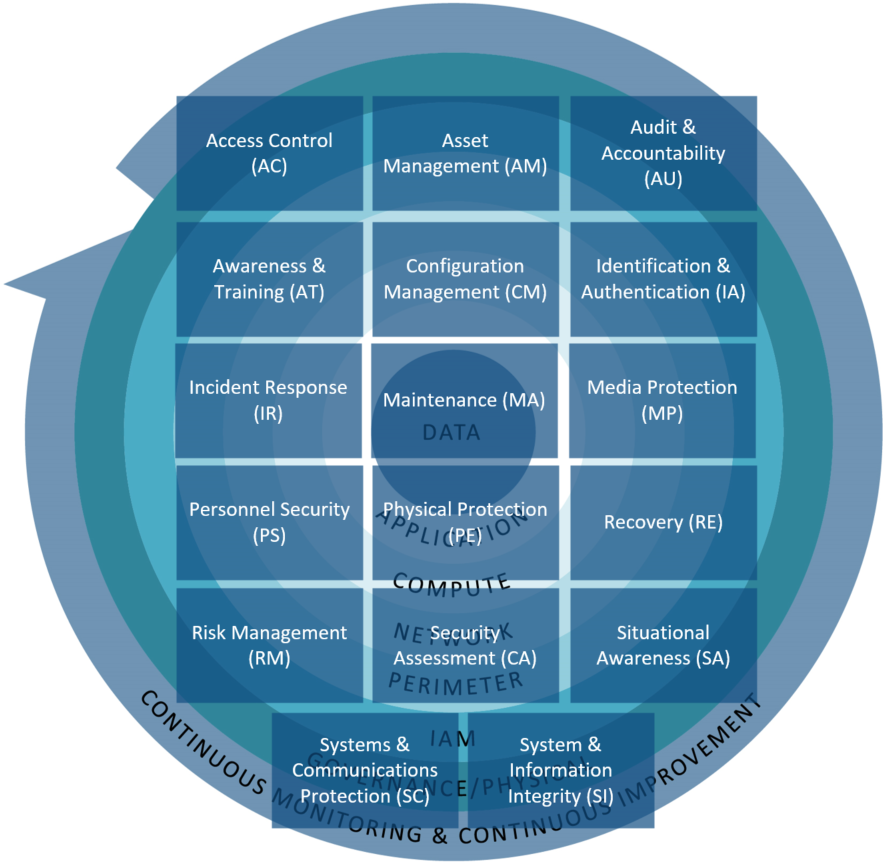
17 CMMC domains (v1.0)
We identify your organization’s information assets, governance, risk management, compliance program needs, & determine appropriate CMMC level to fit business needs.
We work with your organization to take stock of relevant systems, existing governance and system security policies, data traversal patterns, etc.
We conduct a readiness assessment and gap analysis of systems and governance resources and processes against the target CMMC level.
We deliver an SSP, assessment report, POAM, and other governance artifacts pertinent to a complete CMMC compliance package.
We continuously monitor and manage the security profile of your systems & operating environments to timely detect anomalies & events and understand potential impacts & ensure timely response.
We support CMMC C3PAO assessment process on behalf of your organization to ensure all requirements and any remediation tasks are promptly completed.
WE ARE POWERED BY OUR CORE VALUE OF WORK PRODUCT EXCELLENCE
Driven by our core values to assure compliance frameworks and more secure environments.





Get a complete compliance and/or security audit!
See how far you are from reaching your risk management objective(s).






