
Why practice Secure Development & Operations (SecDevOps)?
Security is best when baked into applications and implementing a secure development lifecycle ensures that resulting applications have far fewer vulnerabilities. Learn more.
THE PERILOUS STATE OF DEVELOPMENT & OPERATIONS (DEVOPS)
Application DevOps won’t/can’t secure itself against threats
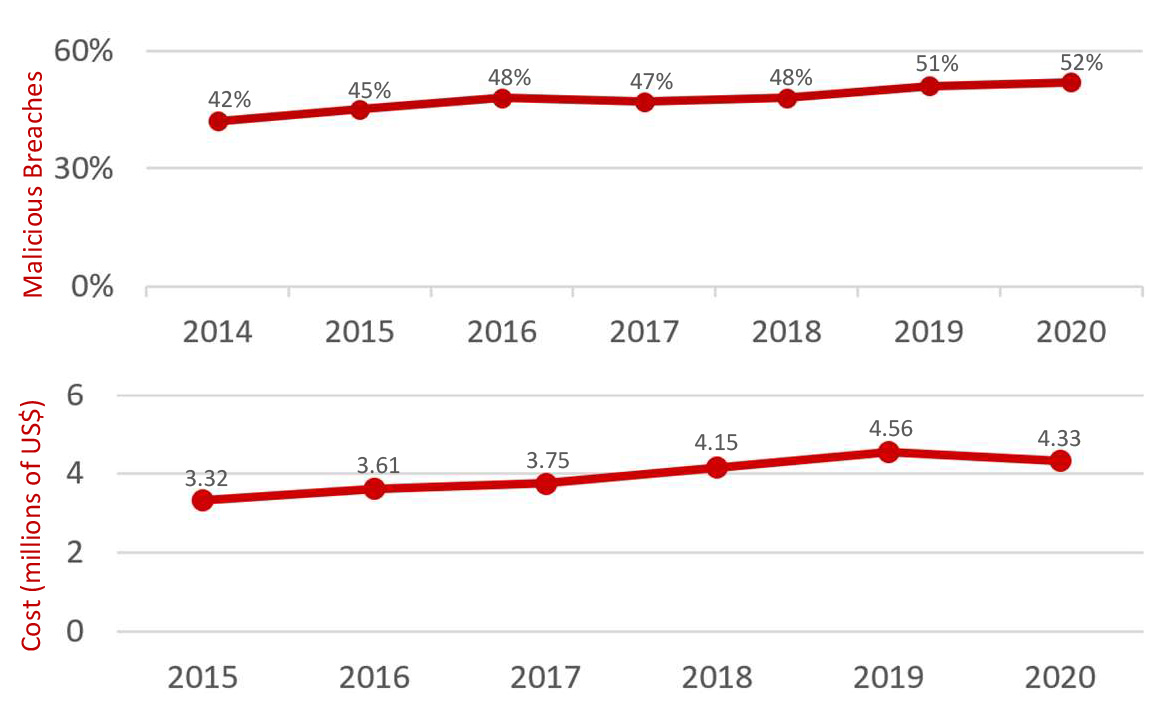
Average cost of breaches and the increase in malicious breaches.
The share of breaches caused by malicious attacks steadily increased over time from 42% in 2014 to 52% in 2020. This 10% increase represents a nearly 24% increase (growth rate) in the share of breaches caused by malicious attacks, according to IBM Security Cost of Data Report.
Over the past six years, the research has also been consistent in showing that breaches are increasingly having much higher costs over time, according to IBM Security Cost of Data Report.
MITIGATE RISKS IN YOUR DEVOPS PIPELINES
Drastically reduce risks in DevOps pipelines for a more secure infrastructure.
Invest in wholistic governance, risk management, security and compliance programs for corporate, cloud, and SecDevOps.
Adopt a zero trust security model at every decision & enforcement point to help prevent unauthorized access to sensitive data.
Minimize the complexity of IT and security environments.
Protect sensitive data in corporate & cloud environments using policy and technology.
Invest in security orchestration, automation, and response (SOAR) to help improve detection and response times.
Stress test your incident response plan to increase cyber resilience.
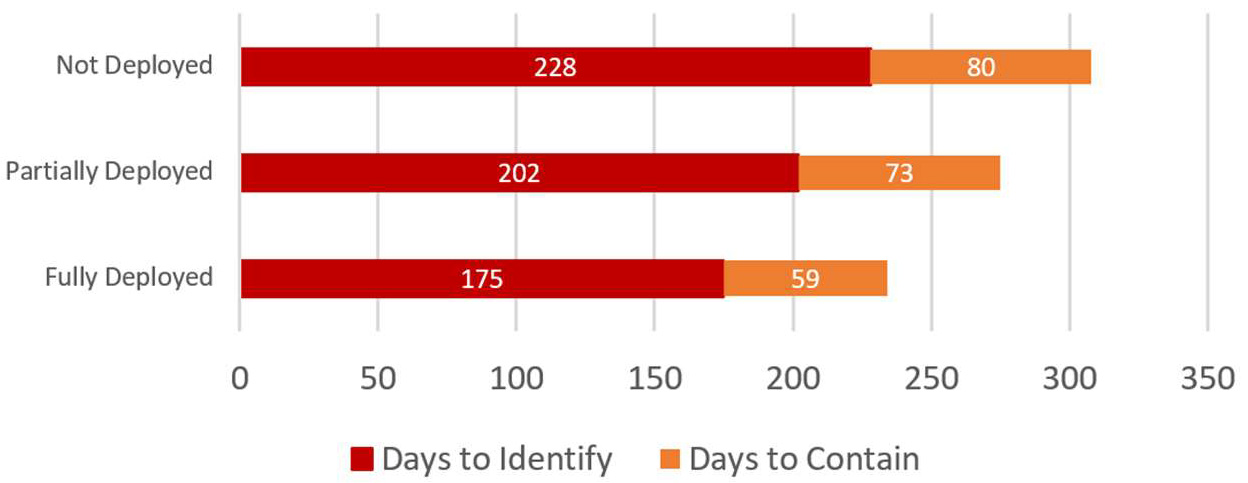
Average time to identify and contain a data breach by level of security automation.
Use tools that help protect and monitor endpoints and remote employees.
Use managed security services to help close the security skills gap or handle the entire process.
WHY HIRE US?
We are best in class in SecDevOps & managed services.
Security Development Lifecycle (SDL)
We provide training to ensure everyone understands security best practices.
We help define and continually update security requirements to reflect changes in functionality and to the regulatory and threat landscape.
We help define metrics and compliance reporting to Identify the minimum acceptable levels of security quality and how engineering teams will be held accountable.
We perform threat modeling to identify security vulnerabilities, determine risk, identify mitigations & controls beyond baseline minimums.
We establish design requirements and define standard security features that all engineers should use.
We define and use cryptography standards to ensure the right cryptographic solutions are used to protect data.
We keep an inventory of third-party components and create a plan to evaluate reported vulnerabilities to manage the security risk of using third-party components.
We define, publish, and use a list of approved tools and their associated security checks.
We integrate into CI/CD and perform Static Analysis Security Testing (SAST) on source code before compiling to validate the use of secure coding policies.
We integrate into CI/CD and perform Dynamic Analysis Security Testing (DAST) run-time verification of fully compiled software to test security of fully integrated and running code.
We perform penetration testing to uncover potential vulnerabilities resulting from coding errors, system configuration faults, or other operational deployment weaknesses.
We establish a standard incident response plan/process to address new threats that can emerge over time, from an assumed breach perspective.
Security at the core/fore of all our work.
Operational Security Assurance (OSA)
We use multi-factor authentication (MFA) to ensure only users who are authorized have access.
We enforce least privilege to provide control and management of sensitive accounts and grant access to services only as needed.
We protect Secrets by implementing a mechanism to inventory, monitor, maintain, and update all stored secrets.
We minimize attack surface by minimizing functionality to only what’s necessary for the service to operate.
We encrypt data in transit and at rest to ensure confidentiality and integrity of data at all times.
We implement security monitoring to ensure security events are audited and monitored.
We implement a security update strategy by continuously scanning for vulnerabilities and keeping software up to date.
We protect against DDOS attacks with real-time mitigation to common network-level attacks to safeguard availability.
We validate the configuration of web applications and sites to ensure web apps maintain optimal security configuration.
We perform penetration testing; simulate real-world attacks and challenge teams to detect, protect, and recover.
WE ARE POWERED BY OUR CORE VALUE OF WORK PRODUCT EXCELLENCE
Driven by our core values to assure compliance frameworks and more secure environments.





Get a complete compliance and/or security audit!
See how far you are from reaching your risk management objective(s).






