
Why should your cloud environments be FedRAMP-compliant?
All businesses with applications, systems, and other assets in the cloud should ensure FedRAMP compliance at minimum but ideally also implement controls for their environments’ unique requirements to minimize security exposure & attack surface.
THE PERILOUS STATE OF CLOUD SECURITY
Malicious actors focus attacks on cloud infrastructures as a treasure trove of vulnerabilities.
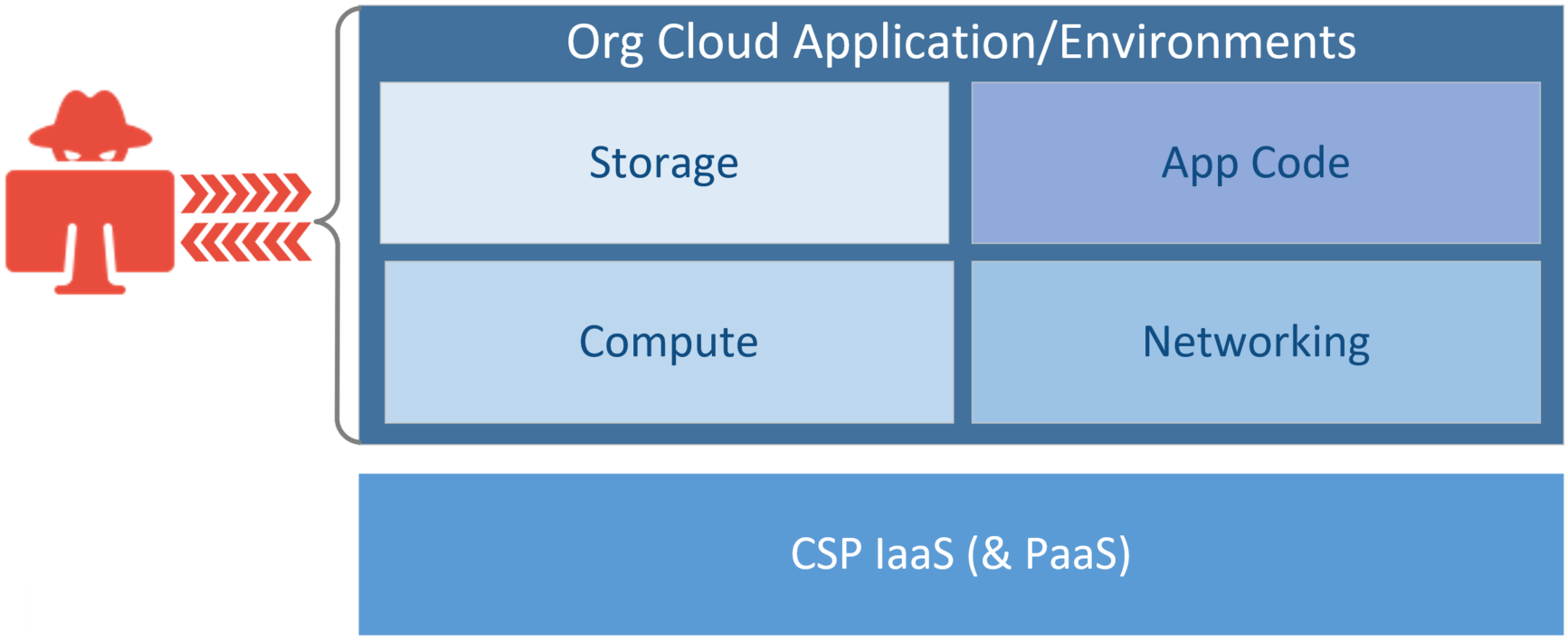
Malicious attackers target organizations’ cloud infrastructure for misconfigurations, errors, and other vulnerabilities.
The exponential growth of malicious attacks on cloud applications is affecting organizations across industries.
Rather than expend resources trying to attack the robust underlying cloud infrastructure that CSPs spare no cost in protecting, malicious actors target organizations’ cloud infrastructures/environments because they know that is where misconfigurations and other errors & vulnerabilities exist.
MITIGATE THE RISK OF DATA BREACHES IN YOUR CLOUD ENVIRONMENTS
Drastically reduce risks in your cloud application operations environments.
Adopt a security development lifecycle (SDL) process that incorporates security with DevOps for a sustainable SecDevOps culture.
Train engineers & developers in secure development practices.
Gather security requirements alongside functional requirements.
Align with FedRAMP baseline requirements.
Threat model to address security requirements unique to your infrastructure in addition to baseline minimums.
Integrate automated SAST and DAST into your CI/CD for continuous security assessments of code development.
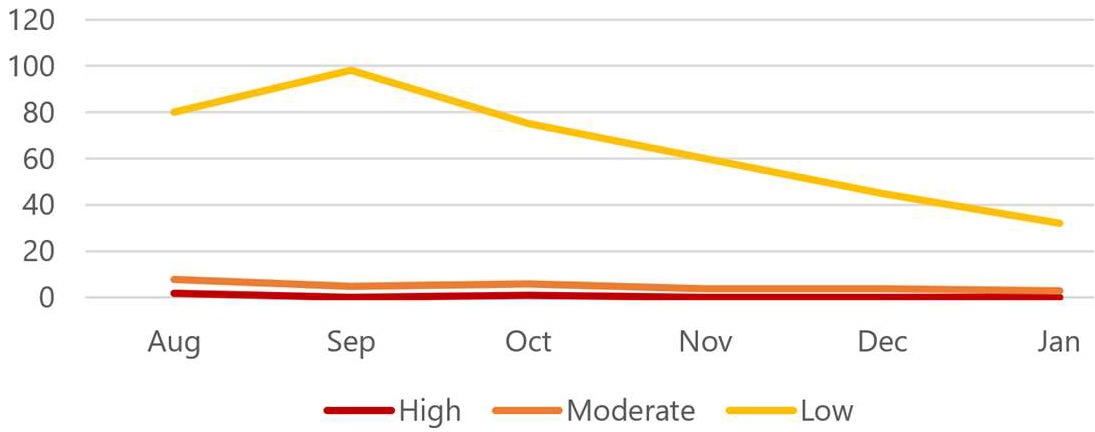
Continuously trend risks/vulnerabilities downwards perpetually.
Adopt Infrastructure as Code (IaC) to automate app infrastructure deployment and compliance processes.
Use managed security services to help close the security skills gap or handle the entire process to offload and avoid burdening your in-house personnel.
WHY HIRE US?
We are best in class in cloud SecDevOps & automation for both FedRAMP JAB & Agency Authorizations.

Our layered security and compliance approach across your cloud environments to continuously meet FedRAMP requirements and beyond.
We work to understand business objectives, mission as well as cloud adoption justification, motivations, and desired outcomes.
We take inventory of your cloud estate, create a cloud adoption plan, determine skills and support readiness for migration or new cloud infrastructure.
We prepare your cloud environment with automation to mitigate the potential for the introduction of human errors and drastically reduce time to authorization (FedRAMP JAB & Agency).
We securely migrate and modernize existing and/or develop new infrastructure.
We support governance establishment, benchmarking and improvement efforts as well as the identification of business risks and risk tolerances definition.
We manage monitoring, operations, resilience, and assessment requirements.
WE ARE POWERED BY OUR CORE VALUE OF WORK PRODUCT EXCELLENCE
Driven by our core values to assure compliance frameworks and more secure environments.





Get a complete compliance and/or security audit!
See how far you are from reaching your risk management objective(s).






