
Why should your organization adopt end-to-end security?
All businesses should ensure the corporate, development, and operations/cloud environments are all secure to avoid gaps that threats can exploit and continuously monitor them for policy compliance. Learn more.
THE PERILOUS STATE OF INFORMATION SECURITY ACROSS ORGANIZATIONAL ENVIRONMENTS
Data breach incidents across organizational environments are on the rise.
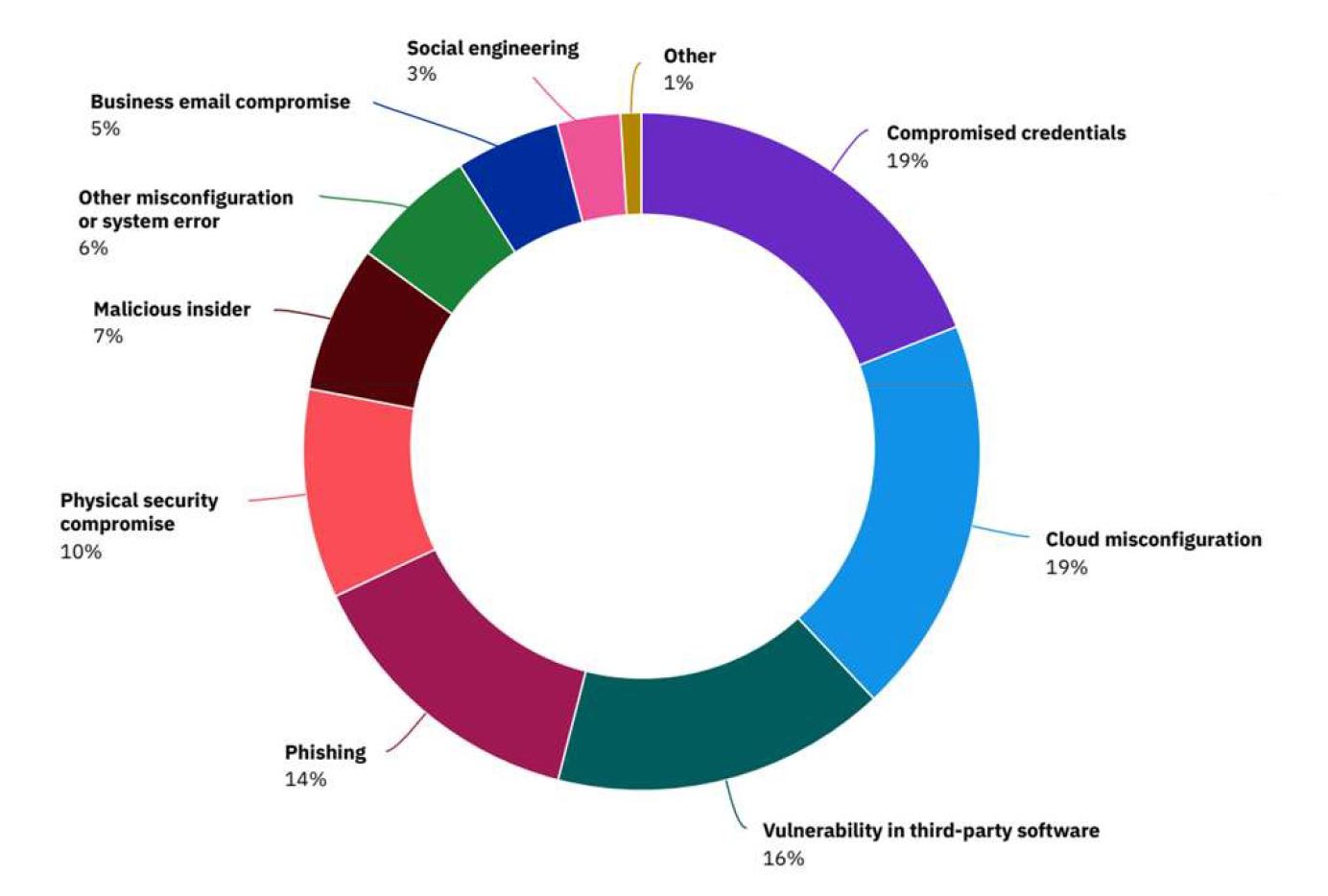
Breakdown of malicious data breach root causes by threat vector.
The exponential growth of data breaches has a widespread of threat vectors and effects across industries with businesses of all sizes right in the center of the storm, according to IBM Security “Cost of Data Breach Report 2020”.
Brand devaluation, lawsuits, fines, regulatory penalties, loss of customer trust and revenue, and various other data breach costs continue to increase as the need to mitigate information security risks persists.
MITIGATE THE RISK OF DATA BREACHES ACROSS YOUR ENVIRONMENTS
Drastically reduce risks in your corporate, development, and operations/cloud environments.
Commit to a wholistic governance, risk management and compliance program for corporate, cloud, and SecDevOps.
Adopt a zero trust security model at every decision and enforcement point to prevent unauthorized access to sensitive data across your environments.
Minimize the complexity of IT and security across your environments.
Protect sensitive data across your environments using policy and technology.
Invest in security orchestration, automation and response (SOAR) to help improve detection and response times.
Stress test your incident response plan across your environments to increase cyber resilience.
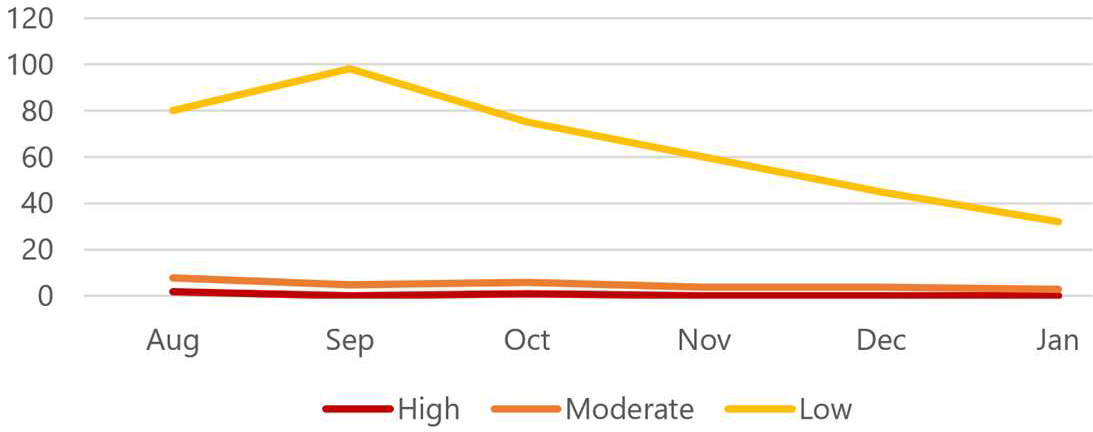
Continuously trend risks/vulnerabilities downwards perpetually
Use tools to continuously protect and monitor the security profile of pertinent systems.
Use managed security services to help close the security skills gap or handle the entire process to offload and avoid burdening your in-house personnel.
WHY HIRE US?
We are best in class in managed security services across environments.
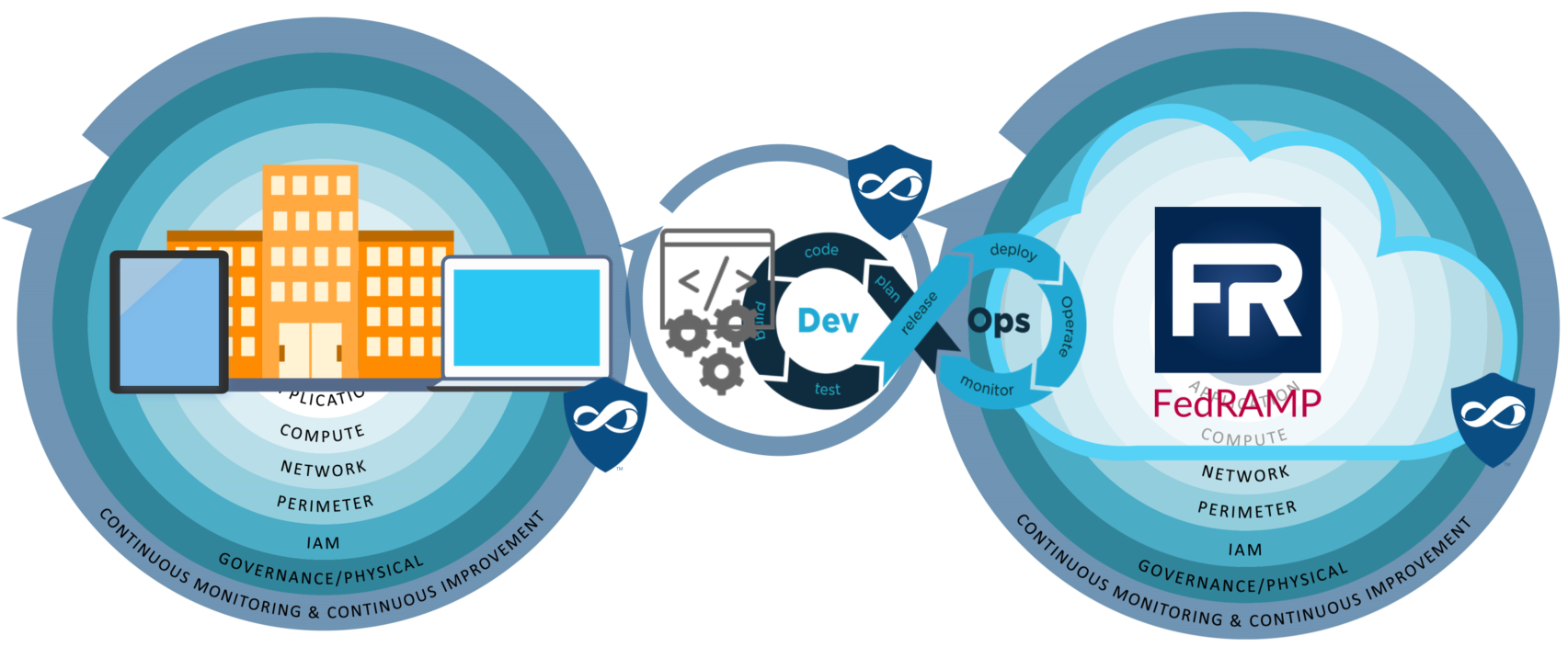
Security across your Corporate, Development, and Operations environments for a seamless end-to-end security framework.
We identify your organization’s information assets, governance, risk management, and compliance program needs.
We establish the necessary governance, risk management, and compliance program requirements across environments and assess & protect your assets.
We continuously monitor your assets across your environments to timely detect anomalies & events and understand the potential impact.
We alert you and swiftly respond accordingly to contain any impact of potential cybersecurity incidents.
We support efforts to quickly recover assets to normal operations to reduce the impact from a cybersecurity incident.
We apply agile continuous improvement methodologies to ensure the ever-evolving threat landscape is mitigated.
WE ARE POWERED BY OUR CORE VALUE OF WORK PRODUCT EXCELLENCE
Driven by our core values to assure compliance frameworks and more secure environments.





Get a complete compliance and/or security audit!
See how far you are from reaching your risk management objective(s).






